Quantum computing isn’t science fiction anymoranymore, it’s a countdown problem. As advances accelerate, the same power that promises exponential progress in data processing could also dismantle the cryptographic systems securing today’s digital world. Algorithms like RSA and ECC, which form the backbone of web authentication, banking transactions, and data exchange, are built on mathematical problems that quantum computers can solve in minutes.
This isn’t a distant threat. State-backed adversaries are already stockpiling encrypted data, waiting for the day it can be decryptedecrypted, a strategy known as “harvest now, decrypt later.” In an era defined by connected web apps and digital identities, post-quantum identity security isn’t an optional upgrade; it’s the only way forward to preserve trust in the web’s foundation.
Quantum Computing’s Real Threat to Web Authentication
The modern web’s trust layer is built on public-key cryptography, where algorithms like RSA and ECC power nearly every authentication handshake from HTTPS to OAuth logins. Their strength lies in computational difficulty: classical computers cannot feasibly reverse-engineer private keys from public ones. Quantum computing, however, introduces a new paradigm where that assumption no longer holds.
Shor’s algorithm, running on a sufficiently advanced quantum machine, can factor large numbers and solve discrete logarithms exponentially faster. This directly breaks RSA and ECC, the foundations of today’s Transport Layer Security (TLS). In other words, the cryptographic roots of web identity are mathematically sound but only until quantum scaling reaches the threshold where those problems become solvable.
At the protocol level, this risk becomes most visible during the TLS handshake, when browsers and servers exchange keys and digital certificates. These steps key exchange and certificate validation are the very moments quantum attacks could unravel, exposing credentials and session data.
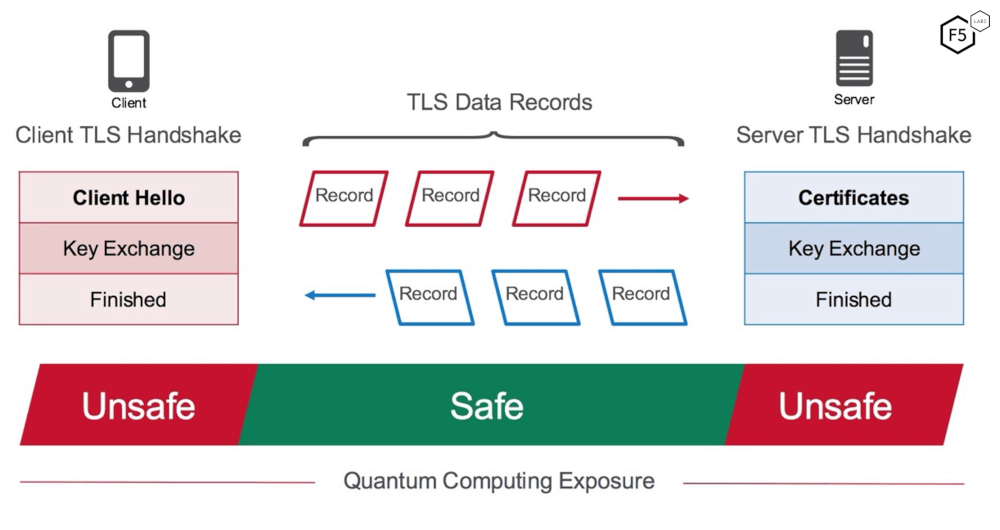
TLS handshake flow highlighting RSA and ECC key exchange as quantum-exposed zones, underscoring where today’s authentication becomes unsafe once quantum decryption is possible. (Source: IBM Research)
The diagram clarifies why current HTTPS and API security are only temporarily safe. The “unsafe” zones mark the handshake boundaries — where public keys are exchanged and validated that would be the first to fail under quantum attacks. This insight matters because even if application data remains encrypted, the identity verification itself can be falsified once those handshake layers are compromised.
What follows is the “harvest now, decrypt later” problem: adversaries can store encrypted web traffic today and decrypt it in the near future, exposing login credentials, certificates, and user tokens long after the attack. According to research by NIST and IBM, more than 70% of enterprise authentication flows still depend on RSA or ECC, making migration to quantum-resistant frameworks a matter of when, not if.
What Post-Quantum Identity Security Really Means
Adopting post-quantum identity isn’t just about upgrading cryptographyptography, it’s about redefining trust across the entire authentication chain. Today’s web applications rely on public-key cryptography (RSA, ECC) to issue and verify digital identities, yet both algorithms are vulnerable to quantum attacks that can reverse-engineer private keys.
A post-quantum identity framework uses quantum-resistant algorithms such as CRYSTALS-Kyber for key exchange and Dilithium for digital signatures. These are being standardized by NIST for integration into protocols like TLS 1.3, OAuth 2.0, and SSH, ensuring that the web’s most common authentication handshakes remain secure even in a post-quantum era.
The transition isn’t theoretical—it reshapes how web applications authenticate and authorize users. Post-quantum identity focuses on crypto-agility and hybrid compatibility:
Crypto-agile architecture: Systems can switch or layer new algorithms without breaking existing trust anchors.
Hybrid models: Classical and quantum-safe keys work together during migration to avoid service disruption.
Hardware-secured credentials: TPMs or HSMs store lattice-based keys, extending quantum resilience to endpoints.
To illustrate where quantum-safe identity protection fits into today’s web authentication systems, consider the modern token-based access flow below:
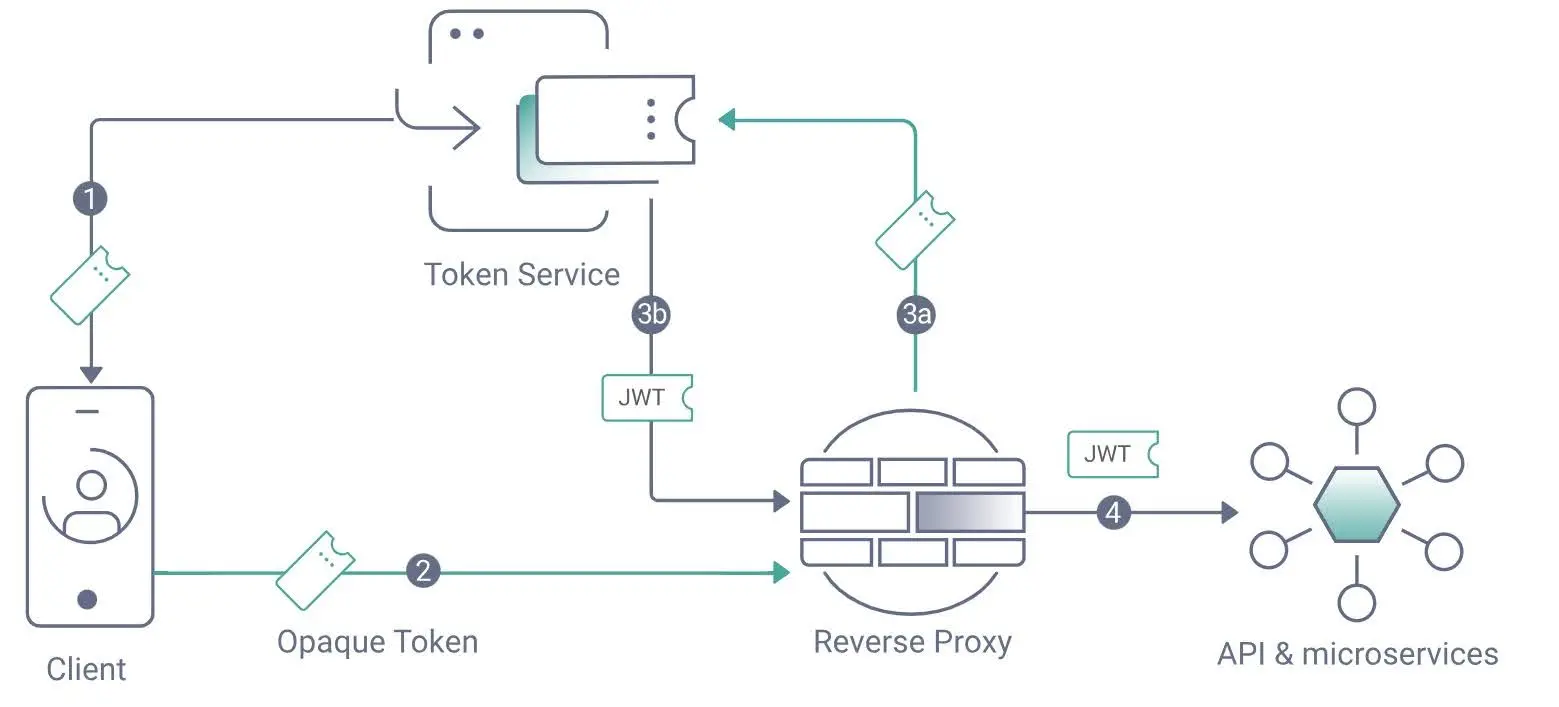
Web authentication flow using token and reverse proxy, showing key points where post-quantum encryption can reinforce identity integrity (Source: Curity Identity Server)
In a traditional flow, clients authenticate through a token service that issues and validates JSON Web Tokens (JWTs) for APIs and microservices. Each exchange key generation, signing, and verification depends on asymmetric encryption. When upgraded with post-quantum algorithms, these same trust checkpoints become resistant to quantum decryption, future-proofing identity assurance for web and enterprise applications alike.
This evolution also intersects with the growing need for AI-assisted security and compliance validation, as explored in this analysis on AI-generated code and compliance guardrails. Together, post-quantum cryptography and AI-based testing frameworks form a dual defense one protecting encryption integrity, the other ensuring code-level resilience against emerging threats.
Architecting Quantum-Safe Systems for Long-Term Trust
The move toward post-quantum identity security is not a distant concerconcern, it’s a present architectural challenge. As enterprises modernize their ecosystems across web platforms and financial networks, long-term trust becomes the true metric of success. The encryption and authentication protocols deployed today must endure through the coming quantum decade, where RSA and ECC will no longer suffice.
To sustain this continuity, organizations need crypto-agile architectures—systems capable of evolving from classical to quantum-safe algorithms without breaking existing integrations. Twendee helps enterprises build this foundation through a phased and architecture-first transition:
Discovery and risk mapping: Locating vulnerable RSA/ECC implementations across APIs, single sign-on (SSO), and payment flows to prioritize critical exposure points.
Integration of quantum-resistant algorithms: Implementing NIST-standardized cryptographic suites like Kyber for encryption and Dilithium for digital signatures, validated for high-load, real-world performance.
Automation in DevSecOps: Embedding continuous cryptographic updates into CI/CD pipelines so that every deployment inherits secure, quantum-ready configurations by default.
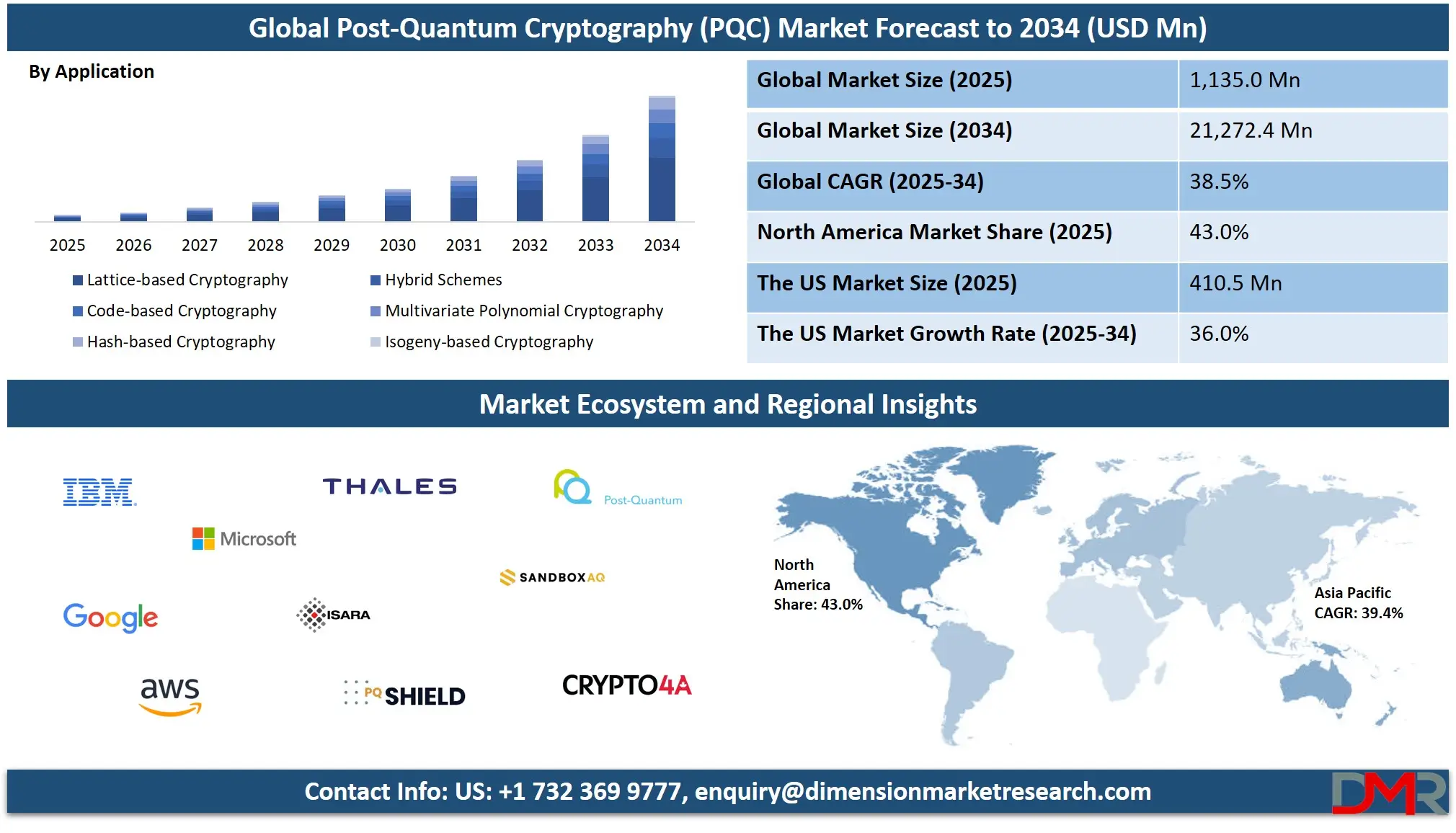
Forecasted growth of post-quantum cryptography adoption through 2034, highlighting enterprise migration toward quantum-safe identity systems and data preservation (Source: Dimension Market Research).
Quantum computing is rewriting the rules of security and enterprises that wait risk rewriting their systems under duress. The shift to post-quantum identity isn’t simply about new encryption; it’s about rethinking how digital trust is built, stored, and scaled.
As cryptography becomes a long-term design principle rather than a short-term safeguard, forward-looking organizations are already restructuring their web authentication frameworks and financial infrastructures to resist quantum threats before they materialize.
Those who invest early in quantum-safe architectures will define the new baseline of secure interaction where every identity, credential, and transaction remains verifiable in a future defined by uncertainty.
Conclusion
Quantum computing is reshaping the foundation of digital trust. The shift to post-quantum identity isn’t just a technical upgradupgrade, it’s an architectural transformation that defines how organizations safeguard data for decades ahead. Enterprises that begin this transition now will lead in security continuity, not react to disruption.
Twendee helps businesses build quantum-safe architectures that preserve identity integrity and long-term resilience across web and financial ecosystems. Explore future-ready security insights and transformation stories with us on LinkedIn and Facebook.
