In 2025, banks will face one of the most disruptive regulatory shifts in over a decade. New global standards on identity assurance, authentication strength, and AML oversight are converging into a single mandate: modernize or risk penalties, service disruption, and loss of customer trust. As fraud accelerates through AI-generated deepfakes and synthetic identities, traditional controls can no longer protect customers or satisfy regulators.
This is the moment when digital identity banking becomes more than a compliance requirement. It becomes the foundation of operational resilience, secure onboarding, and the bank’s ability to function safely at scale. The institutions preparing now will stay ahead. Those that wait will find themselves defending outdated systems in a far more hostile landscape.
Why 2025 Is a Critical Turning Point for Digital Identity Banking
The shift occurring in 2025 is not incremental, it represents a structural break in how banks are expected to verify identities, detect fraud, and demonstrate compliance. Three forces are converging to create unprecedented urgency:
Stricter regulatory standards demand stronger, more transparent identity controls. Global regulators are raising the bar on identity assurance levels, authentication strength, and AML transparency. Requirements such as continuous identity monitoring, real-time reporting, and audit-ready traceability exceed the capabilities of legacy KYC processes and OTP-based authentication. Banks that cannot demonstrate end-to-end control over customer identity will struggle to meet compliance obligations.
AI-driven identity fraud is accelerating faster than traditional controls can respond. Deepfakes, synthetic identities, automated phishing kits, and credential-stuffing bots have evolved beyond what static eKYC or rule-based AML systems can detect. Fraudsters can now mimic biometric cues, forge documents at scale, and exploit weaknesses in SMS-based authentication exposing banks to higher operational risk and regulatory scrutiny.
Failure to modernize carries immediate and measurable consequences. Institutions that fall behind face penalties, restricted onboarding capabilities, increased fraud losses, and potential service disruption during compliance reviews. Operational costs rise as manual investigations overwhelm teams, while customer trust erodes when authentication friction increases or security incidents become public.
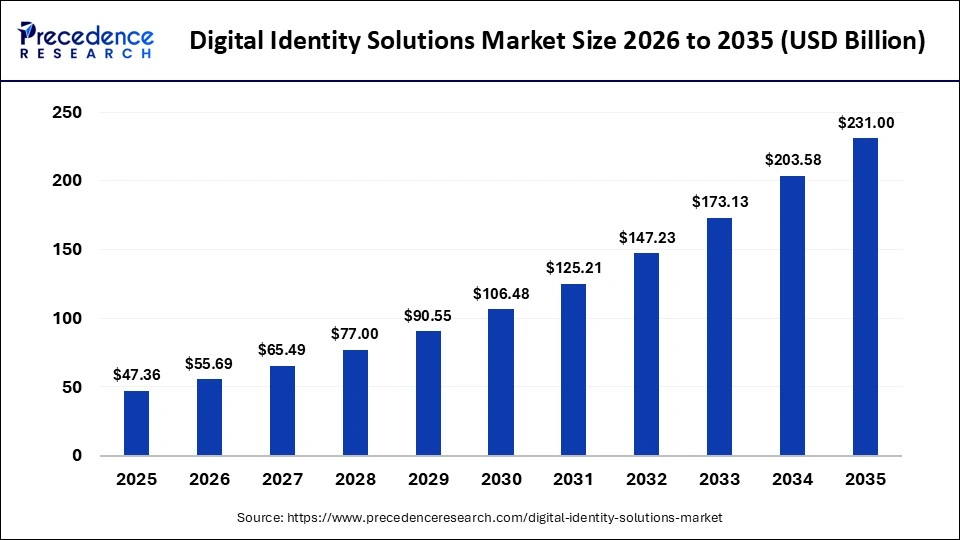
Global spending on digital identity solutions is projected to grow from $47B in 2025 to more than $200B by 2034, reflecting the accelerating regulatory and security pressures facing banks. (source: precedence research)
Altogether, these forces make 2025 a decisive inflection point, one where digital identity banking becomes central to regulatory compliance, operational resilience, and long-term competitiveness.
How Banks Are Preparing for the 2025 Wave of Digital Identity Regulations
Banks are focusing their transformation across five key pillars. Each pillar represents a practical response to what 2025 regulations demand and what modern fraud trends require.
Strengthening Digital Identity Infrastructure
Banks are beginning at the architectural level rebuilding the digital identity layer to support stronger assurance standards, cross-channel consistency, and real-time regulatory visibility. This shift reflects the recognition that compliance in 2025 cannot be achieved by patching individual components; it requires a unified, intelligence-driven identity foundation that spans the entire customer lifecycle. Key investment areas include:
Modern IAM/CIAM platforms that unify identity across mobile, web, ATM networks, and partner APIs. These platforms allow banks to consolidate fragmented identity data, enforce consistent authentication policies, and orchestrate identity flows across legacy and cloud environments. They also enable stronger lifecycle management: onboarding, credential issuance, privilege escalation, and account recovery, all under a single identity governance layer.
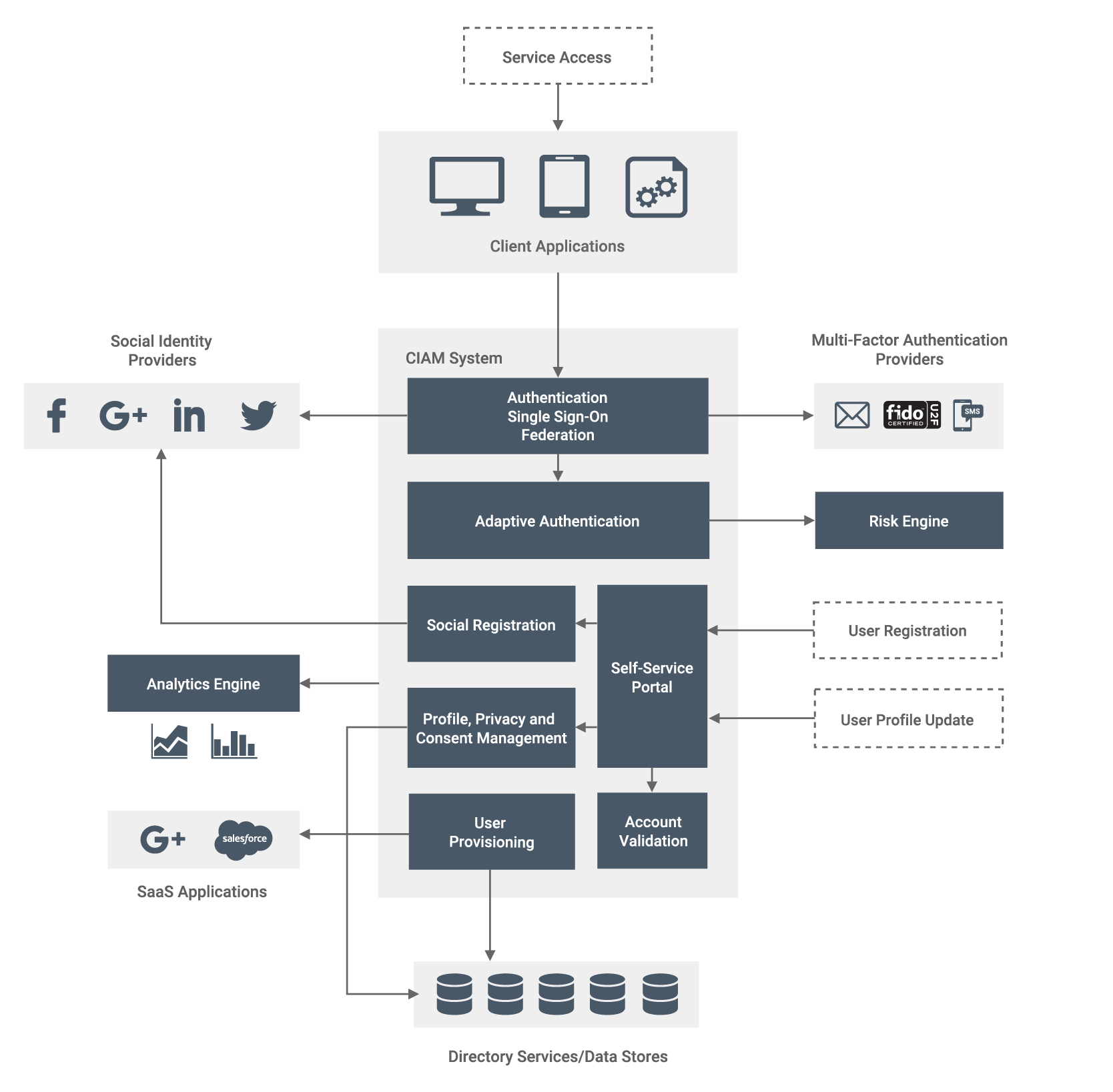
Modern CIAM architecture for digital identity banking, including adaptive authentication, MFA, risk engine, and identity lifecycle management. (source: WSO2)
Continuous identity assurance models, where verification occurs throughout a session, not only at login. Regulators increasingly expect ongoing risk assessment during high-value transactions or changes in user behavior. Banks are implementing systems that evaluate device integrity, session anomalies, biometric re-authentication triggers, and contextual signals in real time ensuring identity remains trustworthy from login to logout.
Enhanced auditability, ensuring every authentication, risk check, and decision is traceable to regulatory requirements. Identity logs must now provide cryptographically verifiable trails that show when, how, and why identity decisions were made. This includes linking risk scores to AML alerts, mapping authentication methods to assurance levels, and maintaining immutable audit trails ready for on-demand regulatory inspection.
For CTOs, this means shifting toward an identity-first architecture: identity becomes the backbone of every interaction, privilege, and risk evaluation. Instead of treating identity as a security feature, banks must elevate it to a core operational system one capable of scaling with fraud trends, regulatory updates, and customer expectations, without compromising performance or availability.
Modernizing KYC/AML to Meet Stricter Compliance Standards
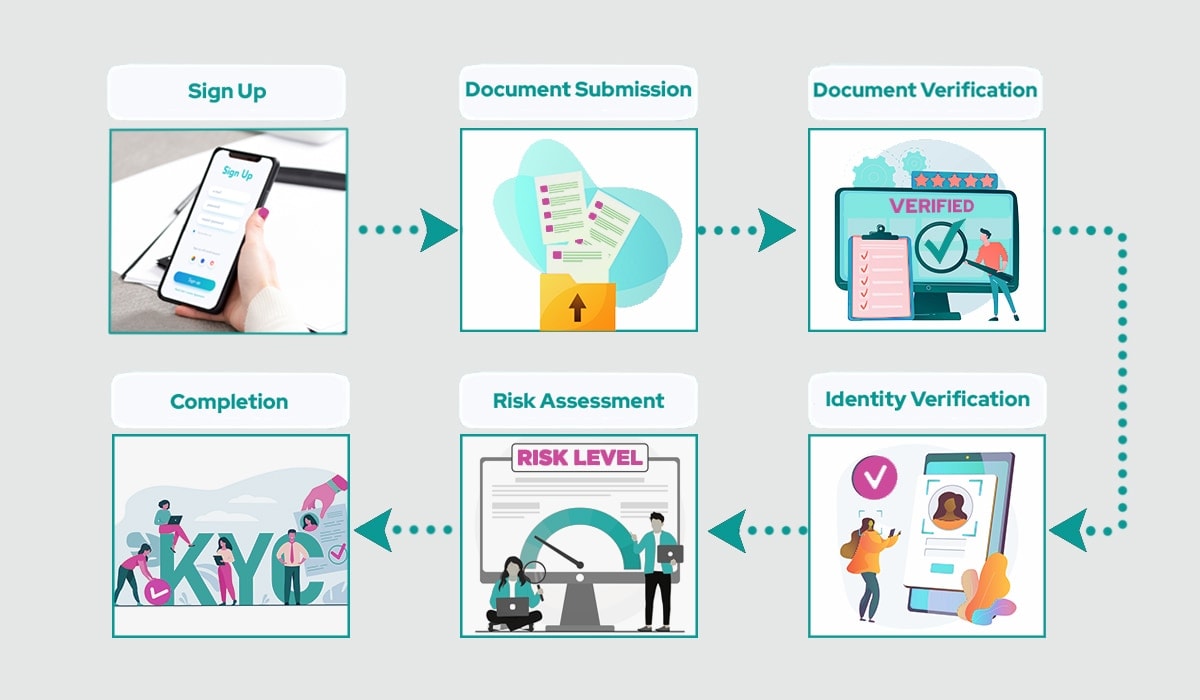
eKYC workflow showing document submission, verification, identity checks, and automated risk assessment (source: aratek)
KYC and AML systems are facing unprecedented regulatory pressure in 2025 as supervisors push banks toward real-time identity validation, automated risk scoring, and transparent auditability. Traditional workflows largely manual, document-based, and batch-processed cannot meet the speed, accuracy, or consistency regulators now expect. As a result, banks are rebuilding their KYC/AML stack to support dynamic risk assessment and fraud detection that adapts continuously to user behavior and emerging threats. Key modernization priorities include:
Advanced eKYC pipelines capable of resisting deepfakes, synthetic IDs, and AI-generated documents. Banks are upgrading biometric engines, deploying multi-angle liveness detection, and integrating document forensics tools that analyze holograms, fonts, and metadata at sub-second speeds. These capabilities ensure that onboarding becomes resilient against modern identity forgery techniques that bypass legacy OCR- or image-based verification.
AI-driven identity risk scoring that updates throughout the customer lifecycle. Instead of treating identity verification as a one-time step, banks now analyze behavioral patterns, device fingerprints, geolocation shifts, and network anomalies continuously. These signals feed into machine-learning risk engines that flag inconsistencies instantly helping compliance teams intervene before a transaction becomes a reportable incident.
Real-time AML monitoring to replace batch reviews and periodic checks. Banks are adopting streaming analytics platforms that evaluate transactions as they occur, correlate them with risk profiles, and automatically escalate suspicious activity to investigators. This real-time capability is increasingly a regulatory expectation not a competitive differentiator and is central to meeting 2025’s reporting standards.
Reducing false positives to lower compliance cost and prevent customer friction. Overly sensitive AML rules create noise that overwhelms analysts, leads to delayed review cycles, and frustrates legitimate customers. Modern machine-learning models reduce operational drag by distinguishing genuine anomalies from predictable patterns, improving both efficiency and regulatory accuracy.
For CTOs, these upgrades signify a shift toward dynamic identity governance, where identity assurance, transaction behavior, and AML controls operate as a unified intelligence layer. This alignment not only strengthens regulatory resilience but also reduces manual workload, enhances customer experience, and positions the bank to respond faster to evolving fraud methodologies.
Moving to Passkeys and Strong Authentication Standards
As regulators tighten authentication requirements and fraudsters exploit weaknesses in SMS-based OTP systems, banks are accelerating the shift toward passkeys and hardware-backed authentication. The 2025 regulatory environment favors methods that are phishing-resistant, device-bound, and cryptographically verifiable standards impossible for traditional OTP or password systems to meet. This transformation is not merely a security enhancement; it is a strategic response to mandates demanding stronger customer authentication (SCA) and higher identity assurance levels. Key transformation areas include:
Replacing OTP/SMS with passkeys built on FIDO2 and public–private key cryptography. Passkeys eliminate the vulnerabilities inherent in SMS channels SIM swapping, interception, OTP forwarding and ensure that authentication occurs within trusted hardware enclaves. This architecture prevents credential replay attacks and aligns directly with regulator expectations for phishing-resistant authentication.
Integrating biometrics as a primary authentication factor backed by secure device-bound credentials. Banks are embedding biometric authentication fingerprint, facial recognition, or voice into passkey flows, ensuring the user is both the legitimate device owner and a verified individual. The combination of biometric verification and hardware-backed keys delivers assurance levels unattainable with static passwords or OTPs.
Applying strong customer authentication (SCA) rules consistently across all channels. 2025 regulations increasingly require banks to enforce SCA not only in digital channels but also across mobile apps, partner integrations, and high-risk actions such as changing account details, approving large transfers, or linking new devices. Passkeys enable this uniform enforcement while minimizing user friction.
Building adaptive authentication flows that adjust to user risk in real time. High-risk scenarios such as new devices, unusual geolocation behavior, or transaction anomalies trigger additional verification layers. Low-risk, trusted scenarios allow seamless login. This adaptive model improves security without penalizing legitimate users, reinforcing both compliance and customer experience.
For CTOs, this shift represents a foundational move toward phishing-resistant authentication ecosystems. Passkeys redefine how identity trust is established, eliminating legacy dependencies on passwords and SMS while enabling a scalable, regulation-aligned security posture. The result is a banking authentication framework that is stronger, more consistent across channels, and built to withstand the sophistication of modern fraud.
Implementing Multi-Factor and Risk-Based Security Controls
As identity threats evolve and regulatory expectations shift toward continuous assurance, banks are moving beyond static MFA models to adopt adaptive, risk-based security frameworks. Traditional MFA, while still valuable, cannot account for dynamic behavioral anomalies, emerging fraud patterns, or contextual risk signals that change from moment to moment. To meet 2025 standards, banks must implement identity controls that respond intelligently to user behavior, device posture, and transaction context. Core areas of investment include:
Deploying risk-based MFA that adjusts verification requirements based on real-time context. This approach analyzes session attributes such as device integrity, IP reputation, behavioral deviations, and transaction value. Low-risk activities proceed seamlessly, while high-risk actions trigger step-up authentication allowing banks to maximize security without increasing customer friction unnecessarily.
Leveraging behavioral biometrics to detect subtle anomalies invisible to traditional security controls. Machine-learning models analyze patterns like typing cadence, touch pressure, mouse movement, and even app navigation paths. These behavioral fingerprints are extremely difficult for fraudsters or bots to replicate, enabling banks to identify account takeovers or session hijacking early long before a transaction becomes irreversible.
Implementing continuous authentication for critical sessions and high-value transactions. Instead of permissioning the user only at login, banks evaluate identity trust throughout the entire interaction. Sudden changes such as device switch, location mismatch, or script-based automation trigger instant verification or session termination, significantly reducing fraud exposure.
Integrating device-level security checks as part of the identity posture. Device biometrics, attestation APIs, jailbreak/root detection, and secure enclave validation help ensure that authentication originates from a trusted environment. These controls reinforce regulator expectations on strong device-bound authentication and safeguard critical financial workflows.
For CTOs, this shift represents the evolution from event-based authentication to identity risk orchestration, a system where security decisions are continuous, contextual, and machine-driven. By adopting risk-based and behavioral identity controls, banks build a resilient defensive layer that aligns with 2025 compliance requirements while delivering a smoother, more secure user experience.
Updating Governance, Audit Processes, and Vendor Integration
Modernizing identity controls is only half the challenge; banks must also transform the governance, audit mechanisms, and vendor ecosystems that support them. Regulators in 2025 expect not just technical compliance, but operational clarity proof that every identity decision is governed by policy, traceable across systems, and defensible under scrutiny. This requires banks to rethink how identity processes are documented, monitored, and executed across internal teams and external partners. Key areas of organizational and operational alignment include:
Updating internal policies to reflect new identity assurance, authentication, and AML expectations. Policy frameworks must explicitly define assurance levels, verification thresholds, escalation paths, and criteria for high-risk identity events. These policies must be consistently applied across digital channels and legacy systems ensuring regulators observe a unified, enforceable approach to identity governance.
Implementing automated audit trails that provide end-to-end transparency. Banks are adopting systems that generate immutable logs linking authentication events, risk scores, AML alerts, and identity decisions. These logs must be searchable, exportable, and aligned with regulatory audit formats allowing compliance teams to demonstrate control within seconds during supervisory reviews.
Consolidating vendor ecosystems to ensure interoperability and policy consistency. KYC vendors, AML engines, passkey providers, fraud detection systems, and orchestration platforms must integrate tightly to avoid policy gaps or inconsistent risk scoring. Banks are increasingly moving toward vendor architectures where identity data, signals, and decision logic flow through a unified identity backbone rather than siloed tools.
Establishing cross-functional governance models between fraud, compliance, security, and engineering teams. The shift to continuous identity assurance requires synchronized decision-making. Banks are formalizing governance councils and operational runbooks to ensure identity risks are escalated consistently and remediation actions are executed quickly across departments.
For CTOs, this evolution represents a transition toward governance-first identity operations where technology, compliance, and risk teams share a common framework for decision-making. By strengthening auditability and aligning vendors under a single policy architecture, banks not only meet 2025 regulatory expectations but also reduce operational fragmentation and accelerate incident response.
Conclusion
The shift taking place in 2025 is more than a compliance update, it is a redefinition of how banks establish trust, protect customers, and prove their governance standards to regulators. Institutions that modernize their digital identity infrastructure early will not only reduce fraud exposure and avoid penalties, but also deliver faster onboarding, stronger authentication, and a more seamless customer experience. Those that delay will find themselves defending outdated systems in an environment that no longer tolerates technical debt, fragmented identity workflows, or reactive compliance.
Twendee partners with banks to accelerate their identity modernization agenda not by adding isolated tools, but by redesigning the foundations that digital identity depends on. We help institutions upgrade their identity infrastructure, architect next-generation KYC/AML workflows, integrate passkey authentication across legacy and mobile environments, and deploy security controls that meet international regulatory standards. Our role is to close the gap between regulatory expectations and real-world system readiness ensuring banks can operate with confidence, resilience, and compliance in 2025 and beyond. Stay connected via Facebook, X, and LinkedIn.
Read our latest blog: Top 5 Software Development Trends Every Business Must Adapt to in 2025
