Modern Web2 applications rarely resemble the systems they were originally secured for. What once consisted of a single web application and a database has evolved into distributed ecosystems of microservices, internal tools, third-party integrations, automation scripts, and API surfaces that often exceed the frontend itself. In this environment, web2 application security is no longer defined by who can log in. It is defined by how systems behave once access is granted, how requests propagate across services, and whether runtime activity aligns with architectural intent. This shift explains why security failures in modern Web2 increasingly occur without any authentication bypass.
What “security challenges” mean in modern Web2 applications
In modern Web2 architectures, security challenges no longer stem primarily from unauthorized access. Instead, they arise from the growing gap between static access control models and dynamic, distributed system behavior. Traditional Web security assumed that risk emerged when attackers bypassed authentication or escalated privileges. By contrast, modern Web2 systems frequently fail under very different conditions:
Access is legitimate
Credentials and roles are valid
Requests conform to defined permissions
Yet the overall system behavior deviates from what the architecture was designed to allow. This pattern is increasingly common in environments built on microservices, APIs, automation, and third-party integrations. Once access is granted, actions can be executed at machine speed, chained across services, and applied to objects at a scale that static permission models were never designed to evaluate.
Industry data reflects the impact of this shift. The average cost of a data breach reached USD 4.88 million, according to the IBM Cost of a Data Breach Report 2024, underscoring how operational misuse, not just intrusion, drives real business damage. This marks a structural change in how enterprise application security must be understood: from controlling entry points to understanding and constraining behavior after access is granted.
Importantly, this evolution is also reshaping how regulators and enterprises think about digital identity governance. As explored in our analysis on how banks are preparing for the 2025 wave of digital identity regulations identity controls alone are no longer sufficient without stronger guarantees around how authenticated access is exercised across systems. This marks a structural change in how enterprise application security must be understood: from controlling entry points to understanding and constraining behavior after access is granted.
Why role-based models are breaking down in Web2 application security
Role-based access control (RBAC) remains a foundational mechanism in most Web2 systems. However, it was designed for environments where identities were relatively stable, permissions were predictable, and actions were discrete and human-driven.
Modern Web2 violates all three assumptions.
Dimension | Role-based security | Behavior-based security |
Primary signal | Assigned roles | Runtime behavior |
Context awareness | Limited | High |
API misuse detection | Weak | Strong |
Business logic abuse | Not addressed | Actively detected |
Suitability for modern Web2 | Declining | Increasing |
RBAC answers a necessary but narrow question: is this identity allowed to perform this action? Behavior-based security addresses a broader and increasingly critical one: does this action make sense in the current system context?
This distinction explains why valid credentials have become such a powerful attack vector. The Verizon Data Breach Investigations Report (DBIR) shows that stolen credentials are involved in 88% of basic web application attacks, highlighting the limits of identity-only security models once access has already been obtained. In other words, modern Web2 systems are not failing because roles are misassigned. They are failing because roles alone cannot describe intent, sequence, scale, or abnormal usage patterns.
Across enterprise Web2 environments, the same structural warning signs appear consistently:
Security decisions rely primarily on RBAC
APIs are protected only at the endpoint level, without object-level controls
Internal services and APIs are treated as implicitly trusted
Service accounts hold long-lived, broad permissions
No baseline exists for what “normal” system or API behavior looks like
When several of these conditions apply, security failures are no longer isolated incidents. They become predictable outcomes of system design. This diagnosis aligns with broader industry consensus. The OWASP API Security Top 10 (2023) ranks Broken Object Level Authorization (BOLA) as the number one API risk, reinforcing that many modern failures occur after authentication succeeds, when systems cannot distinguish acceptable behavior from dangerous misuse.
Where modern Web2 security actually fails
1. Enterprise application security risks are no longer user-centric
In enterprise environments, threats increasingly originate from the reality of complexity: fragmented ownership, sprawling permissions, and systems that evolve faster than governance. This is why enterprise application security cannot be treated as “a better RBAC spreadsheet.”
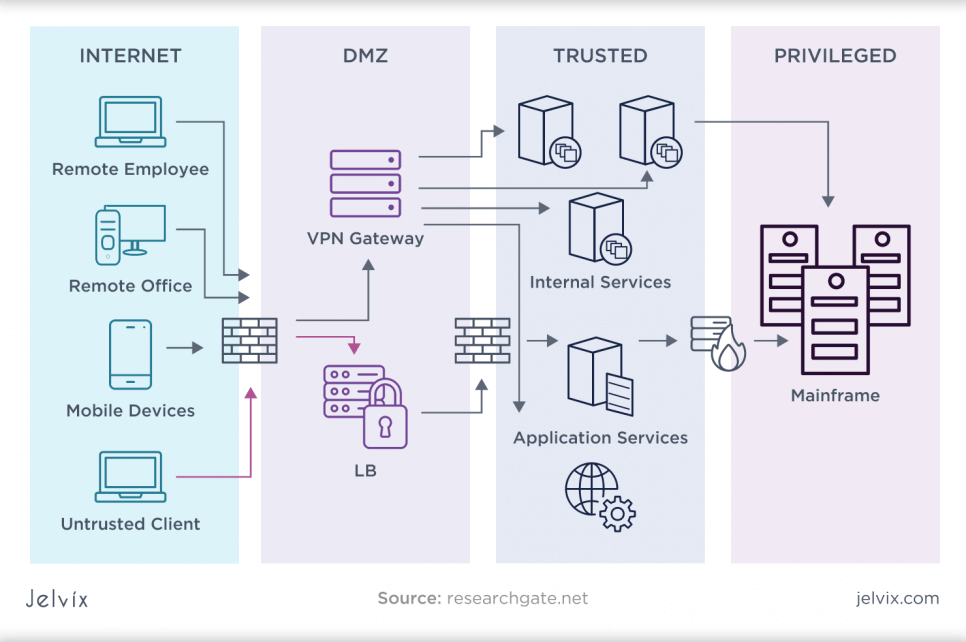
Enterprise application security risks across internal system layers (source: jelvix)
Enterprise Web2 systems accumulate permissions over time. Teams add roles to unblock delivery, grant temporary access during incidents, create service accounts for integrations, and rarely revisit what was granted. Over months, those permissions become “permission debt”: an invisible liability that expands the blast radius of any credential compromise or internal misuse.
RBAC can represent permissions, but it does not manage the lifecycle of permissions. It does not naturally answer:
Which privileges are used in practice versus only granted “just in case”?
Which roles are now effectively “super-roles” due to accumulated entitlements?
Which internal services have privileges that were never reviewed after architecture changes?
Enterprise Web2 architecture creates opportunities for lateral movement: a compromise in one area becomes access to adjacent systems via internal APIs, shared secrets, or overly-trusting service calls. Modern attackers do not need to “break in” repeatedly; they move through the architecture the way normal traffic does. This is not theoretical. In Salt Security’s “State of API Security” reporting, 13% of attack attempts explicitly targeted internal APIs, showing that internal surfaces are part of the threat model, not a safe zone.If internal APIs are treated as “trusted” while only external endpoints are hardened, enterprise systems become vulnerable to misuse from inside the perimeter.
Many access-control decisions that look safe in development become risky at scale. Rate limits become too permissive to avoid harming user experience. Debug endpoints survive longer than intended. Logging is incomplete across microservices. Incident response introduces emergency permissions that persist. None of these failures are “RBAC problems” in isolation. They are system design problems that create security failure modes.
This is where behavior-based approaches are practical. Instead of trying to predict every risky permission combination, security can focus on the patterns that create real damage: abnormal data access, suspicious request sequences, unexpected resource traversal, and anomalous service-to-service behavior.
2. API security risks are the largest blind spot
If Web2 used to be “web pages served to users,” it is now “APIs powering everything.” That shift changes the attack surface. APIs are designed for programmatic access, and programmatic access is easier to scale, automate, and abuse. The data reflects how widespread the issue is. Akamai reports that 84% of security professionals experienced an API security incident in the past 12 months (as of its 2024 research), marking an all-time high in that study.When API incidents are that common, the question is not whether APIs matter, but whether the security model matches API reality.
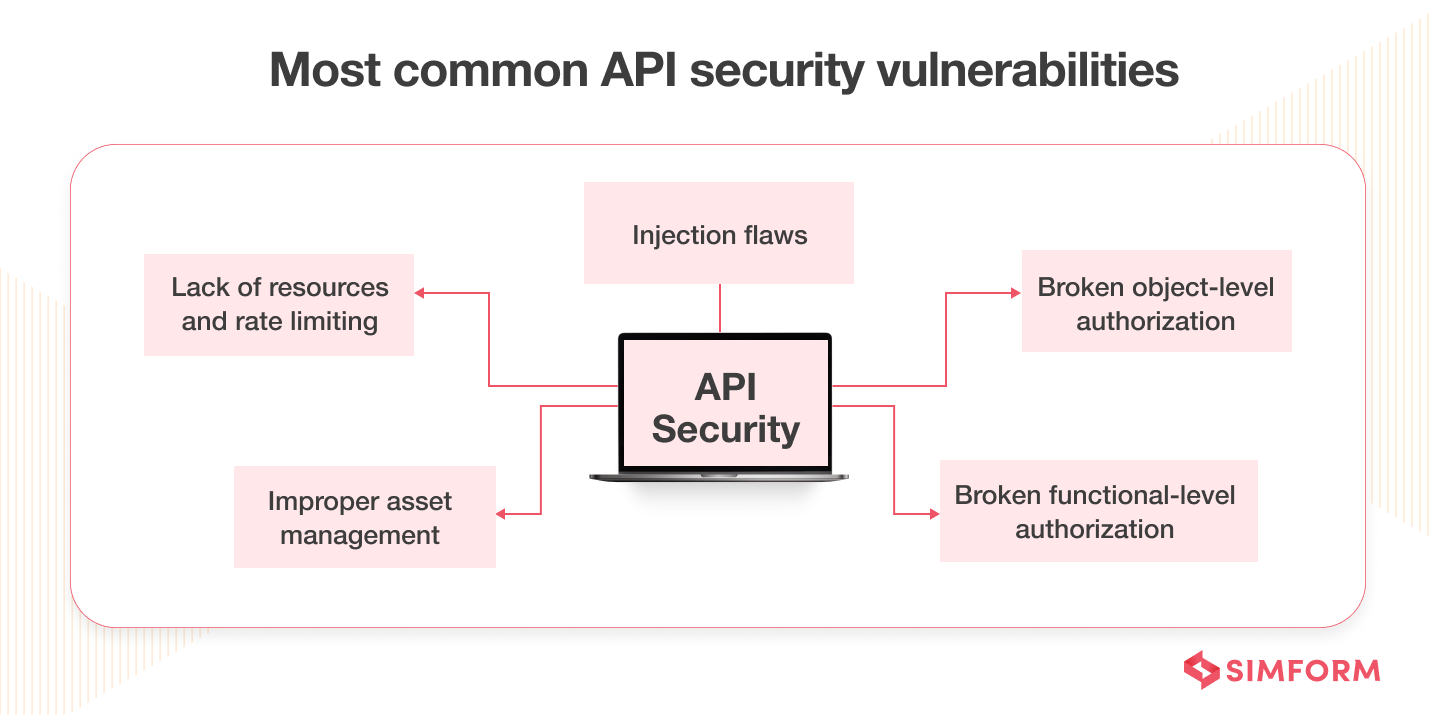
API security blind spots across gateway and backend layers (Source: Simform)
APIs expose functionality, not just data. RBAC typically answers: “Is this caller allowed to access this endpoint?” But API risk often lives in areas RBAC does not naturally capture:
Object-level authorization failures (BOLA): OWASP identifies “Broken Object Level Authorization” (API1:2023) as a top API risk, where attackers manipulate object IDs to access resources they should not. This often happens even when the caller is authenticated and has a valid role. The failure is not identity. The failure is verifying that the caller is authorized for that object.
Property-level authorization and data exposure: OWASP also calls out “Broken Object Property Level Authorization” (API3:2023), where sensitive fields become accessible because the API exposes more than intended.RBAC rarely governs “which fields within the object are safe in this context,” especially across multiple client types (admin dashboards, customer apps, partner integrations).
Authentication and token misuse at scale: OWASP’s “Broken Authentication” (API2:2023) describes patterns such as credential stuffing, weak password controls, and token handling flaws.Even if RBAC is correct, tokens and sessions can be abused programmatically, at high volume, in ways that look “authorized” from a role standpoint.
Some of the most damaging API abuses are business-logic exploits: sequences of valid calls that produce unintended outcomes. Examples include promo abuse, refund loops, inventory reservation attacks, and account takeover workflows that exploit weak step-up authentication.
RBAC cannot detect that the sequence is malicious. It does not know that the velocity is abnormal. It does not know that the pattern is inconsistent with normal behavior. Behavior-based security exists to fill that gap by monitoring how APIs are used, not only whether they are callable.
3. Behavior-based security as the missing layer
Behavior-based security is often misunderstood as “ML for security.” In practice, it is a design stance: security policies should reflect expected behavior across the system, not only identity attributes.
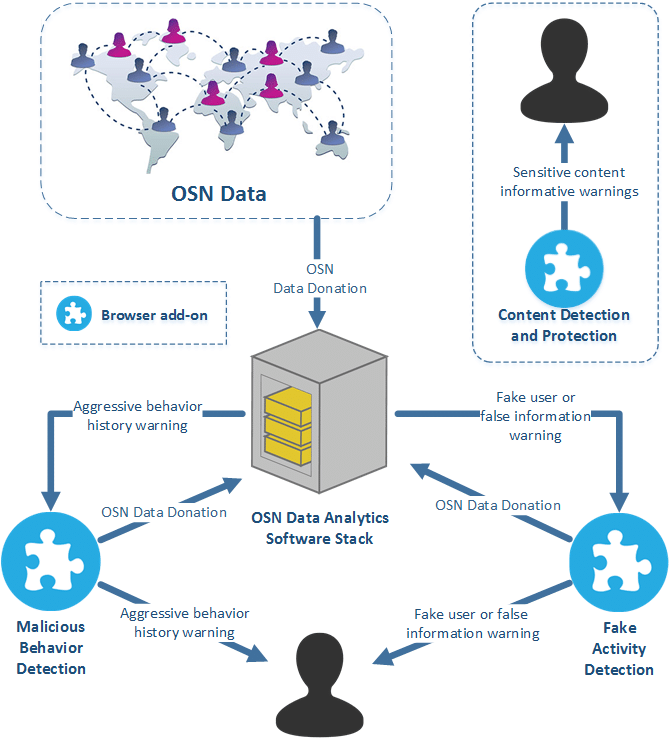
Behavior-based security detecting abnormal system activity (Source: ResearchGate)
At an enterprise level, behavior-based security often relies on a few practical primitives:
Baseline and anomaly detection: establish normal patterns for identities, service accounts, endpoints, and data objects, then flag deviations.
Sequence awareness: detect suspicious workflows, not just single requests (for example, unusual chains of endpoints that rarely appear together).
Context signals: incorporate time, geo, device posture, token age, service origin, and dependency context.
Risk scoring and step-up controls: when behavior is suspicious, require additional verification, reduce privileges, or throttle actions rather than blocking everything.
This layer complements RBAC. RBAC remains useful for coarse-grained permission boundaries. Behavior-based security addresses the reality that modern attackers often operate inside those boundaries once they have credentials or tokens.
Building security layers from behavior and architecture
For teams building or modernizing enterprise-grade Web2 systems, security is most effective when it is treated as part of the system architecture, not as a tool added at the end of delivery. We approach Web2 application security from this premise: protection must reflect how systems are designed and how they behave in real operation, not just how access is defined. Rather than relying solely on perimeter defenses or role assignments, we help organizations build a security layer grounded in architectural awareness and behavioral signals, allowing controls to scale with system complexity.
In practice, this approach includes several core elements.
First, we apply architecture-informed threat modeling across services, APIs, and data flows, including internal APIs that are often overlooked. In modern Web2 environments, these internal surfaces are part of the real attack surface, where blind spots frequently emerge.
Second, we introduce behavioral controls on critical paths, focusing on high-impact actions such as data exports, account changes, payment flows, administrative operations, and partner integrations. Instead of treating every authorized action as safe, we assess whether actions occur in expected sequences, frequencies, and contexts.
Third, we align API security hardening with real-world risk patterns, mapping controls to known failure modes such as Broken Object Level Authorization (BOLA) and broken authentication, while ensuring object-level and property-level authorization are consistently enforced.
Finally, we prioritize operational visibility and response readiness. By focusing on behavioral anomalies rather than raw event volume, abnormal activity can trigger actionable responses instead of noise, which is critical in environments where credential-based compromise remains common.
The objective is not to replace existing IAM or RBAC investments. Those controls remain necessary. The objective is to close the modern Web2 security gap: legitimate identities producing illegitimate outcomes.
Conclusion
Security challenges in modern Web2 applications are no longer driven primarily by unauthorized access. They stem from a deeper mismatch between static permission models and dynamic system behavior in API-driven, distributed architectures. Role-based controls remain necessary, but on their own, they are insufficient to address misuse that occurs after access is granted.
Effective web2 application security today requires visibility into how systems behave in real operation, how actions propagate across services, and how legitimate credentials can still lead to harmful outcomes. Treating security as an architectural layer, reinforced by behavior-based signals, allows organizations to reduce risk without constraining scale or agility.
At Twendee, we work with enterprises to design and implement security layers that are rooted in system architecture and informed by real-world behavior helping Web2 platforms close the gap between access control and actual risk as systems grow more complex.
Stay connected with us via Facebook, X, and LinkedIn.
